Update: Há uma versão em português.
Who still remembers ICQ, AIM and MSN? My first messenger was ICQ and I liked the fact that it was instant. In those days, I didn’t think much about security and was probably too young anyway. We can count ourselves lucky if those tools even used transport encryption. This means that our messages are encrypted on the way from our computer to the server, so nobody can see the content of the messages while they are in transit.
Whoever has access to the server however can know the content since all messages get decrypted as soon as they arrive at the server and then encrypted again before they leave the server for the recipient.
Those days are long gone. We have smartphones now and there are plenty of new apps that replaced the instant messengers of the past. Many of those apps haven’t even used simple transport encryption in the beginning and have been criticized for it. Security became a selling point and even more so after Snowden’s revelations. So let’s fast-forward a bit.
Recent Security Innovations
Many companies have finally realized that if they have our messages in plain text, they attract others who also want those messages. The most powerful of those adversaries have ways to get hold of our conversations, be it by hacking into the servers or by using the law. So the service providers started to deploy end-to-end encryption similar to what PGP does for email. In contrast to transport encryption, end-to-end encryption ensures that the message can only by read by its sender and the intended recipient. It is never decrypted along the way and if stored on a server, even the server’s owner can not read the messages.
That is at least the idea. It needs to be implemented properly and you need to make sure that nobody else gets access to the private keys that secure the communication. As soon as that happens and an adversary has your private key, he can decrypt all your past communication. That is why the concept of forward-secrecy has been introduced. It prevents exactly that from happening by encrypting your communication with fresh session keys as often as possible. These ephemeral keys can not be broken, even if the adversary gets hold of your long term private key.
Looking at Some Popular Messengers
 Let’s look at some messaging apps that people use today. There’s Telegram for example. It uses only transport encryption by default. Then it even stores all your messages on their server, so that when you reinstall the app on another phone, you get all your messages back. How convenient! But that also means that whoever has access to Telegram’s server (or manages to register with your phone number) gets access to all your conversations as well.
Let’s look at some messaging apps that people use today. There’s Telegram for example. It uses only transport encryption by default. Then it even stores all your messages on their server, so that when you reinstall the app on another phone, you get all your messages back. How convenient! But that also means that whoever has access to Telegram’s server (or manages to register with your phone number) gets access to all your conversations as well.
Telegram has a secret chat mode as well that you need to activate specifically to gain end-to-end encryption and forward-secrecy. People who know more about cryptography than me have looked into their crypto and even they don’t know exactly what Telegram is doing there. Although, there is no known weakness of the “secure” chats, I personally wouldn’t even trust those to be secure.
 Then there’s Signal. That’s what everybody (including Edward Snowden) is recommending and it is great. The signal crypto protocol (formally called Axolotl) is awesome. It finally solves many tricky problems that made using good encryption so difficult for so long. For example, if you need a private key to secure your communication and you want to chat from a different device with the same account, how do you get your private key to your other device? How do you communicate asynchronously with somebody who might be offline and therefore can not do a key exchange? All these problems, the Signal protocols solves elegantly.
Then there’s Signal. That’s what everybody (including Edward Snowden) is recommending and it is great. The signal crypto protocol (formally called Axolotl) is awesome. It finally solves many tricky problems that made using good encryption so difficult for so long. For example, if you need a private key to secure your communication and you want to chat from a different device with the same account, how do you get your private key to your other device? How do you communicate asynchronously with somebody who might be offline and therefore can not do a key exchange? All these problems, the Signal protocols solves elegantly.
With Signal, the crypto is solid and gets out of your way. It is easy to use and secure by default. That is why everybody is recommending it and depending on your threat model, I would recommend it as well.
 Then there’s WhatsApp which is the messenger that most people use. It had big security problems in the past, but got a lot better. They contracted Moxie Marlinspike from Signal who helped them to implement the Signal protocol. It got activated for WhatsApp on Android a while ago already and recently was activated on iPhones as well. That’s great since it brought strong and good end-to-end crypto to billions of people.
Then there’s WhatsApp which is the messenger that most people use. It had big security problems in the past, but got a lot better. They contracted Moxie Marlinspike from Signal who helped them to implement the Signal protocol. It got activated for WhatsApp on Android a while ago already and recently was activated on iPhones as well. That’s great since it brought strong and good end-to-end crypto to billions of people.
Unfortunately, WhatsApp is not Free Software, so we can not inspect the source code, make sure it is good and we can’t build our own version of WhatsApp to make sure the source code actually corresponds to the binary. It would be easy for WhatsApp to ship an update that leaks information and conversations from people that law enforcement is currently interested in. Would it be Free Software with reproducible builds like Signal is, that wouldn’t be possible. So security-wise WhatsApp is probably still better than Telegram, but I still wouldn’t trust it.
Like with Telegram’s secret chats, Signal and WhatsApp also give you the ability to make sure the person you are talking to is actually who you think you are talking to. Let me call this Authentication. It is typically done by scanning a QR code or comparing a digital fingerprint. Most messengers use a trust-on-first-use (TOFU) approach which means that your contact is considered to be authenticated from the beginning. You can only discover that you are actually talking to a man-in-the-middle when you scan the QR code.
WhatsApp does not even warn you by default when your contacts’ keys change. This enables an attacker to take over your WhatsApp account with a hijacked SMS and see what people are writing you.
So to summarize, when assessing the security of messengers, we are typically looking at these criteria:
- End-to-End Encryption
- Authentication
- Forward-Secrecy
- Free Software
If you are interested in knowing whether your favorite messenger fulfills these criteria or not, check out EFF’s Secure Messaging Scorecard.
Centralization vs. Federation
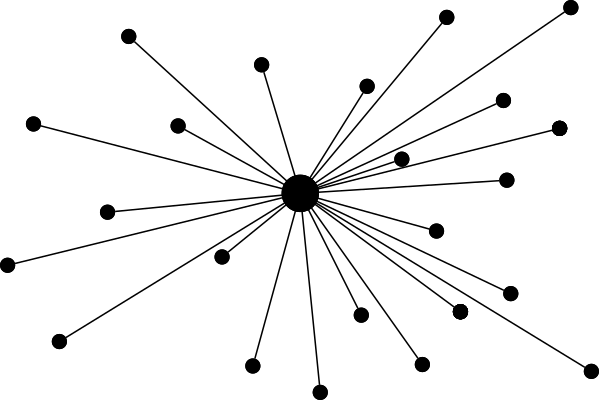
The basic architecture of all the popular messengers is monolithic and centralized. There’s one server (or a cluster of those) that everybody has to connect to. These services are walled gardens where the company running the service has total control over what’s happening. They can not only hand out your metadata, but also exclude you from using the service cutting you off from all your friends. They can require you to use only their non-free software, show you their ads, etc. But even if they don’t bother you and just let you use their service, others have an easy time to block a centralized service entirely. Like Brazil did when WhatsApp couldn’t disclose the information Brazilian judges wanted, because the suspects were already using WhatsApp with end-to-end encryption.
That is why federated architectures have been popular once. The most famous example for that is email. There’s not only Gmail, but many other email servers in the world. You can choose the email provider you like. Everybody is free to open one and it will just work with all the others. You can send emails to everybody no matter on which server they are and nobody can exclude you from using email or dictate the software you have to use.
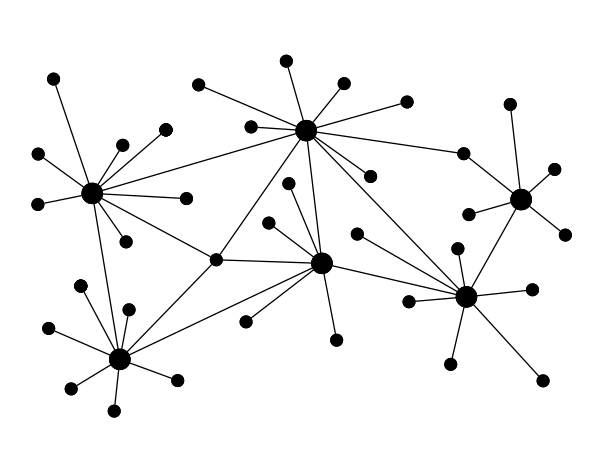
The equivalent to that in the messaging world is XMPP or Jabber. It works great and was once even supported by Facebook, Google and Microsoft. But they have decided again that walled-gardens are better for their business model, so they dropped XMPP like a hot potato. Signal supported federation initially, but decided that it can not make changes fast enough to stay competitive if it has to federate with others.
What about security with XMPP? Well, it is like with email. In the beginning, it was just (optional) transport encryption and even today many servers exchange messages with each other unencrypted or at least potentially unencrypted. Security had to be added later on top of what was already there. For email that was PGP, for Jabber it was OTR. When it came out, it was great. Good security properties and even does deniability. Many people are still recommending it today, but the truth is that it is a pain to use especially when you have more than one device. It also requires both parties to be online when they want to chat encrypted and is just not well integrated in the overall chat experience.
OTR is nowhere near the ease of use the Signal protocol offers, but thankfully the latter has been brought to the XMPP world under the name of OMEMO by the Conversations team. Conversations is an Android app for XMPP. Actually, it is the best XMPP app I know. Give it a try! Unfortunately, OMEMO is not activated by default since many people still use XMPP without it. But this will hopefully change soon. Then Conversations will be a good match to the centralized competition.
What is missing?
So we came a long way and now have better and more secure tools to use than we had just a year ago. That’s great, but we can still do better.
Even if the server can’t read your messages anymore due to end-to-end encryption, it still knows who your friends are and how often you talk to them. That’s usually called metadata and can be more dangerous than the content of the messages. It can be used to map entire social groups and to identity its key people. We know that there’s organizations on this world that kill people based on metadata. So if your adversaries include these organizations and you still like to communicate, you’ve got a problem.
While federation is great in principle, it is not perfect. While a lot harder to censor and block, the metadata is still there and is even seen by more servers. Heck, you still need somebody to run a server for you. Why? Aren’t we all equal in the internet? Couldn’t we connect directly to each other without the need for servers?
That is exactly what a decentralized architecture or peer-to-peer does. You might know that from Bittorrent. It works great there, why not for messaging as well? After all a message is a lot smaller than a HD movie. Do we really need servers that keep track of our activities? Maybe not, let’s find out!
But first, let’s extend the list of criteria for evaluating messengers. We’ve got messengers that fulfill the earlier criteria already, so let’s raise the bar:
- End-to-End Encryption
- Authentication
- Forward-Secrecy
- Free Software
- Censorship Resistant
- No Metadata
Most messengers currently fail at the last two criteria.
Meet Briar
 Now it is time to finally meet Briar which does work completely peer-to-peer without the need for servers and is all about protecting your metadata. It is fully Free Software and utilizes end-to-end encryption with forward secrecy.
Now it is time to finally meet Briar which does work completely peer-to-peer without the need for servers and is all about protecting your metadata. It is fully Free Software and utilizes end-to-end encryption with forward secrecy.
Briar doesn’t require you to upload your entire address book to someone’s server. In fact, it doesn’t even allow that to not disclose your metadata. Instead, it goes back to the good old personal connections. You add your first contacts by meeting them face-to-face to establish maximum trust by scanning each others QR codes. Your communication is authenticated right from the start and you can always be sure who you are talking to.
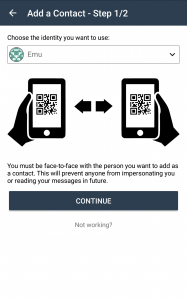 Those who can not meet in person can be introduced by a common friend. This way a web-of-trust is built naturally without needing to manually sign any keys. Others options to add contacts will be added later.
Those who can not meet in person can be introduced by a common friend. This way a web-of-trust is built naturally without needing to manually sign any keys. Others options to add contacts will be added later.
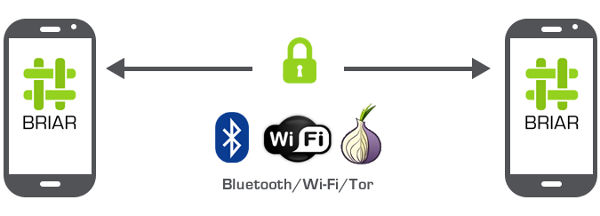
Briar never makes direct connections to your contacts. This would leak metadata. Instead, it runs a Tor Hidden Service on your phone and connects to your contact’s hidden services through the Tor network which anonymizes your connections. An outside observer can not say who is talking to who. They just see that you are making a connection into the Tor network, but that’s all. You could call Briar a Darknet Messenger if you are into this term.
But Briar even works without Internet by using Bluetooth or WiFi. When your contacts are near, Briar recognizes them and establishes a secure connection over which it transmits all messages. So even when the Brazilian government shuts down the mobile internet to inhibit protests during the Olympics, people can still communicate using Briar. It provides maximum defenses against censorship and blocking.

Let me reiterate: With Briar, your data is not stored somewhere in the “cloud” one someone else’s computer, but only encrypted on your device. You choose with whom you share what data and nobody knows with whom you are sharing it with. Takedown orders can have no effect, because every user in a forum for example keeps a copy of its content, so there is no single point where a forum post can be deleted. Also, there can be no denial of service attacks, because Briar has no central server to attack, and everyone has access to all content even if offline.
Briar’s goal is to “enable people in any country to create safe spaces where they can debate any topic, plan events, and organize social movements”. To do this, it needs to be much more than just a messenger and it is! Its architecture is quite generic and it allows for all sorts of other applications to be built on top of it. Messaging is just the first easy show-case application, but of course an important one.
When can I try it myself? Briar is not ready yet. Have a look at the roadmap and the wiki for documentation and ways to help us to get a public beta out faster. Of course, you can always compile the source code yourself if you are really curious. Otherwise, just spread the word a stay tuned for more!
Disclaimer: I am currently working part-time for Briar, so I might be biased on its awesomeness.
2 comments
Comments are closed.